How safe is your Outlook Reading Pane?
The reading pane in outlook is slightly safer than to use than opening a message. The reason for this is that no active content is allowed to run within the reading pane. The same applies to the attachments, since technically it shouldn’t allow active content to run either, however we suggest to be cautious of viewing attachments when the email doesn’t appear legitimate. There has been no reading pane exploits in the last 14 years, since Outlook 2000 SP1.
Unless you are using an email client or web browser which contains an unpatched security hole malicious emails can exploit, you’re fine. This shouldn’t be the case though as you should be using an up-to-date email client and web browser.
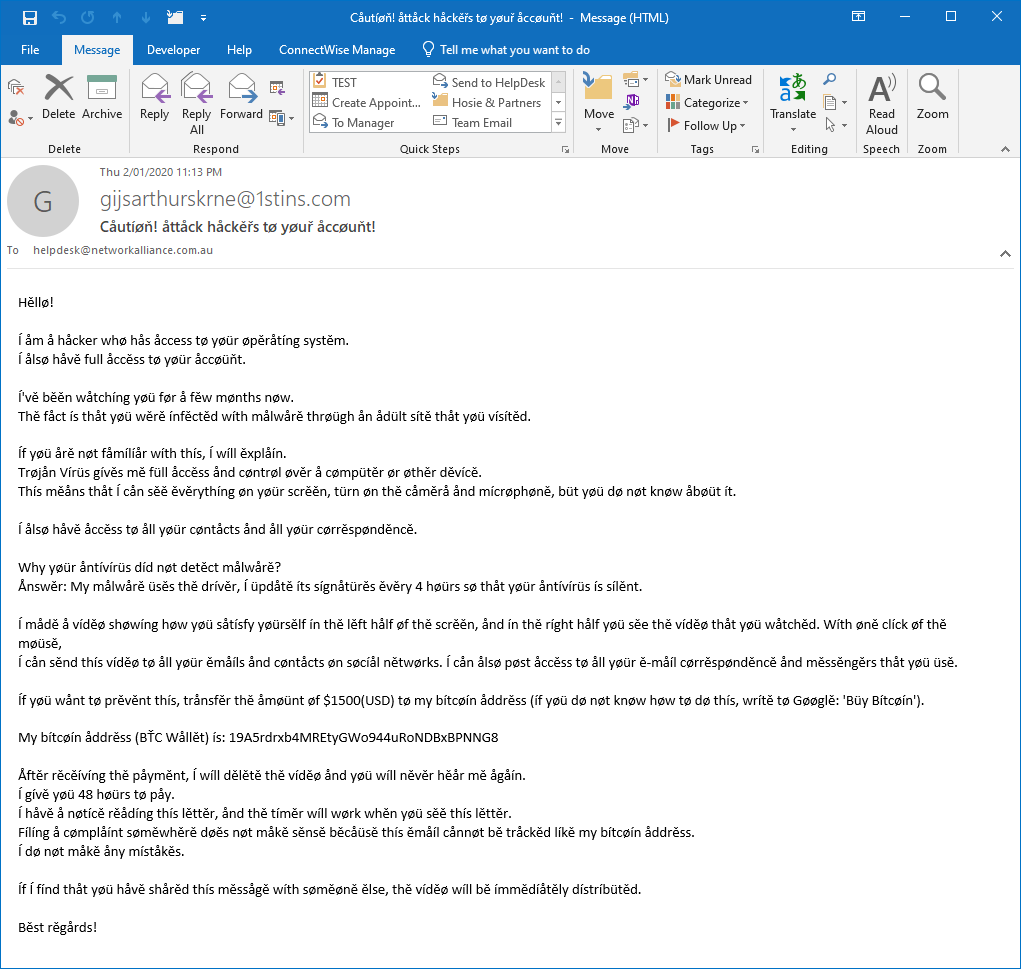
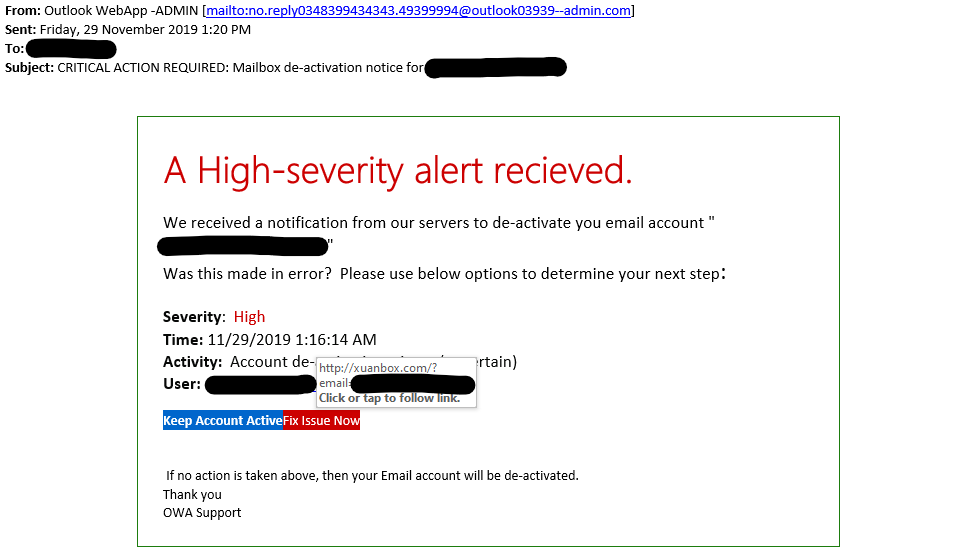
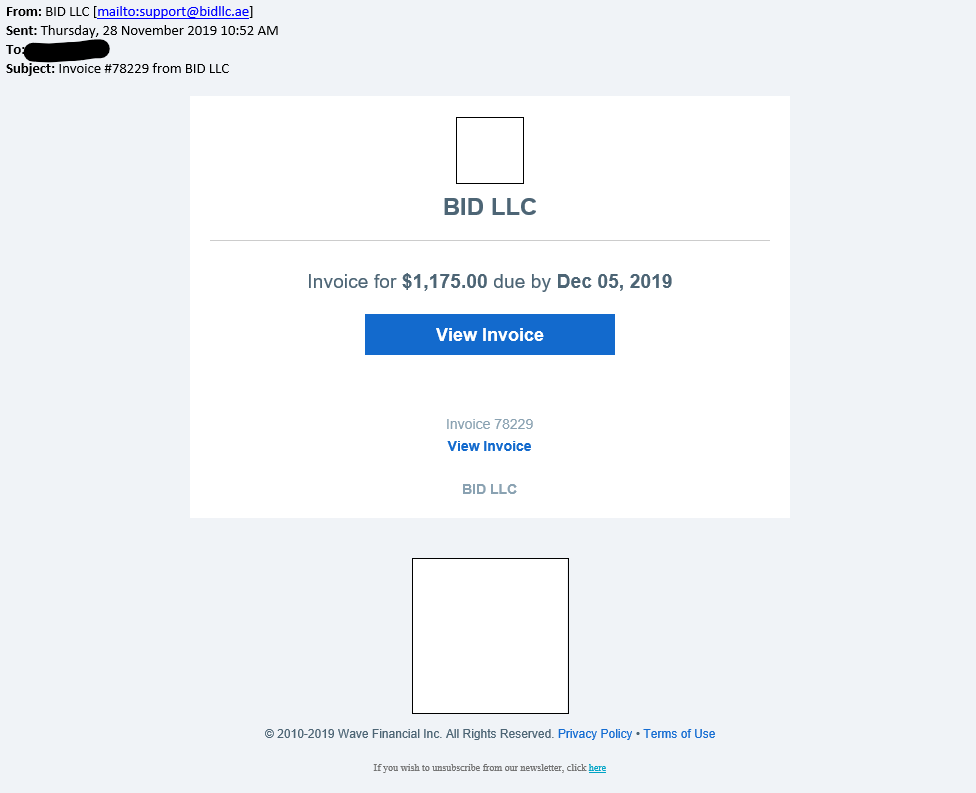
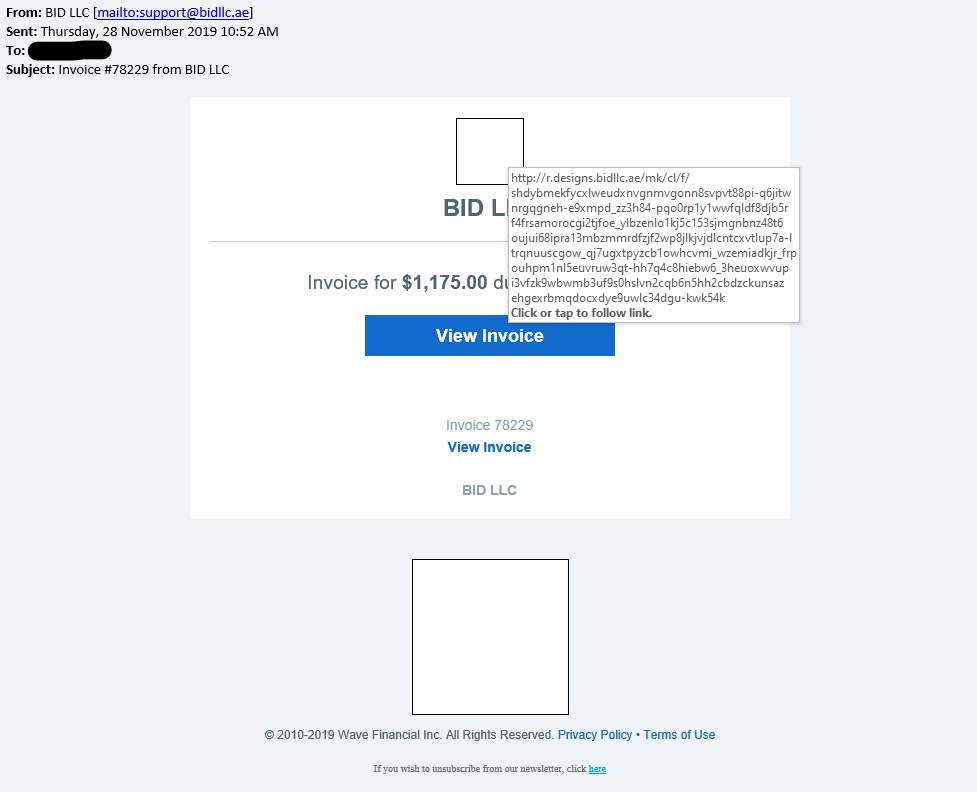
The real risk comes from following phishing links and opening dangerous attachments. The risks are the same whether you are using a desktop application like Microsoft Outlook or any web based email client, like Gmail.
There is usually a common denominator in most infections: the users need to perform a specific action to activate the exploit. In some cases, they need to visit a specially crafted web page and click a link. Unless a popular site is hacked and compromised with this vulnerability, the user will need to be tricked into visiting the site and clicking. In either case, the problem isn’t with Outlook and it’s not something Microsoft can control.
Is opening an Email safe?
Emails are basically text or HTML documents. Just like opening a text file or web page in your browser should be safe, so should opening an email message. If you are using Hotmail, Gmail, Outlook, Yahoo or any other email client – even a suspicious one – it should be safe. Some emails may try to infect you after you open them. They might contain malicious programs disguised as attachments, or have links to malicious websites which contain malware or scams. You should only open trustworthy attachments and be on the look out for suspicious attachments (such as .js, .exe or .com).
Was opening Emails once unsafe?
In the past, Microsoft Outlook had a serious security problem. Emails which were once just plain text were also allowed to contain HTML code: the same code that web pages like this one are written in. An Outlook vulnerability allowed emails to run JavaScript code and infect your computer. For this reason, just opening an email was potentially dangerous.
However, this vulnerability was fixed. Emails cannot use JavaScript. Modern email clients don’t even automatically display images in emails. As with web browsers, operating systems, and other computer programs, security holes are occasionally discovered and patched.
As long as you are using up-to-date software, including your mail client, browser, browser plugins, and operating system – you should be able to open email messages and view them without fear.
Email Safety Tips
File attachments and links in email can still present a real danger. Follow these best practices to stay safe:
- Keep Your Mail Client, Web Browser, and Operating System Updated: Software updates are important, as the bad guys regularly find holes and try to exploit them. Software updates close these holes and protect you. If you are running an outdated browser and email client, you could be compromised. (If you have Java installed, you should uninstall it or at least disable the browser plugin to protect yourself, too.)
- Use Antivirus Software: On Windows, antivirus software is an important layer of protection. It can help protect you from both mistakes and software bugs that allow malware to run without your permission.
- Don’t Run Dangerous Attachments: If you get a PDF file from someone, it’s probably safe to open (especially if your PDF reader is up-to-date). However, if you suddenly get an email with a .exe file or another potentially dangerous type of file you aren’t expecting, even if it’s from someone you know, you probably shouldn’t run the attachment. Exercise extreme caution with email attachments as they are still a common source of infection.
- Be Careful of Links: Clicking links should be safe, just as loading a website in your browser should be safe. However, if the link looks like it leads to a site packed with malware and potentially scams, you probably shouldn’t click it. If you do click a link, don’t download and run any potentially dangerous files. You should also watch out for phishing, if you click a link in an email that appears to be from your bank and end up on a similar-looking website, it may not actually be your bank’s website, but a clever imposter.